![]()
The same SQL software found on voting machines in Michigan and Pennsylvania is likely on the voting machines in Arizona and Georgia.
Earlier this month, The Gateway Pundit covered The Epoch Times article on an Election System Analysis performed on Fulton County Pennsylvania voting systems.
The review was conducted by Wake Technology Services, Inc. (‘Wake TSI’), whose report detailed the presence of Microsoft SQL Server Data Tools (‘SSDT’), on the Dominion Election Management System (‘EMS’) server.
From page 25 of Wake TSI’s report:
…Dominion has installed the Microsoft SQL Server Data Tools (SSDT) on the server. This software is not part of the EAC (Election Assistance Commission) certified configuration and makes the system certification invalid”
For context, the voting system (in this case Dominion):
there is “no valid reason” for the software to be installed on the system and that the presence “allows any user with access to change and manipulate the EMS databases without logging [recording] to the Database, EMS, or [operating system] logfiles.”
The Gateway Pundit exclusively reported that the software found in Fulton County, PA is the same software that Michigan Attorney Matthew DePerno’s team discovered on the Dominion Election Management Server (EMS) in Antrim County MI.
Developing: The Same Suspicious SQL Software Discovered in Michigan Dominion Voting Machines Was Just Found in Pennsylvania Dominion Voting Machines
It now appears there is a high likelihood the same unapproved, separately installed software will be found in Arizona and Georgia.
After reviewing both states contracts with Dominion, we found this on page 25 of Arizona’s contract that the Microsoft Server Management Tools are present in the contract:
![]()
Similarly, we found the same verbiage on page 49 of Georgia’s contract:
![]()
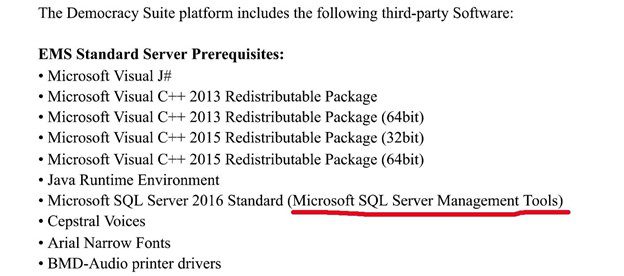
It is important to note that the Microsoft SQL Server Management Tools software is NOT included in the Dominion Democracy Suite 5.5A certified configuration approved by the EAC shown below:
![]()
In a court briefing on May 3, 2021, DePerno stated:
Cyber Ninjas discovered a Microsoft SQL Server Management Studio implant on the system.
“This piece of software is not approved by the Election Assistance Commission (‘EAC’) and allows a user to actually circumvent security protocol and make ‘direct edit entries within the database’ which ‘could potentially be utilized to change vote values.’”
DePerno released the video of systems vulnerability expert Jeffrey Lenberg demonstrating the ability to alter the data in the database, in effect changing the election results using the unapproved software. We included the same video where Lenberg shows how easy it is to alter votes.
EXCLUSIVE: YES, SQL Found on Voting Machines in PA and MI Indicates Election Data Could Be Read and/or Manipulated
The fact that the successful test included an actual Dominion machine and EMS software configuration that was used in the election is immensely powerful evidence. This shows the threat posed by the presence of the software is not just theoretical or remotely possible under unrealistic conditions, but very real under actual conditions.
To better understand the capabilities and potential implications of this software tool, it is important to provide some context.
In each voting precinct or jurisdiction, there are voting machines and/or tabulators that process the ballots. To manage the election there is an Election Management Server, or ‘EMS’ which is simply a Dell computer running the Dominion software program ‘Dominion Democracy Suite 5.5A’. This program receives the data from the voting machines and uses a database program on the same computer, that organizes and stores the data.
The database should only be accessed through the Dominion Democracy Suite 5.5A software and is essentially the “gatekeeper” to the data which is managed according to its own rules and procedures.
This is the configuration that is “certified” or approved by the Election Assistance Commission.
Microsoft SQL Server Management Studio (SSMS) or Microsoft SQL Server Data Tools (SSDT), the software discovered on the Election Management Servers in MI and PA, and most likely will be discovered in GA and AZ are programs that give direct access to the data and completely circumvent the Democracy Suite application. These programs are essentially a “back door” allowing the user unrestricted access to invisibly edit or manipulate the data in the database (votes) without being logged, registered, or controlled by the Democracy Suite program.
Experts know that Microsoft SSDT is a powerful collection of tools used to manage databases and their content, which is a task that only Dominion Democracy Suite 5.5A should have in this configuration.
Wake TSI’s report described it like this:
There is no valid reason for Microsoft SQL Server Data Tools (SSDT) to be installed on the EMS. This software toolbox allows any user with access to change and manipulate the EMS databases without logging (recording) to the Database, EMS or OS logfiles.”
There is simply NO REASON, (no good reason), for this software to be on the same server as the Dominion software. Essentially, it is analogous to a shady business having two sets of books organized automatically in real-time.
There’s more. Microsoft SSDT provides the medium in which to run programming scripts and complex algorithms consistent with the results shown in TGP’s “Drop and Roll”. Additionally, the SSDT suite is capable of far more complex tasks. For example, Microsoft’s SSDT can compare and synchronize data.
In short, the Microsoft SQL Data Tools and the Microsoft SQL Server Management Studio are perfect for coordinating results consistent with those shown in DePerno’s filing.
The post The Same Unapproved SQL Software Found on Michigan and Pennsylvania Voting Systems Is Likely Also on Machines in Arizona and Georgia appeared first on The Gateway Pundit.
via The Gateway Pundit
Enjoy this article? Read the full version at the authors website: https://www.thegatewaypundit.com