Accessing the Cloud
One of the many strangenesses of the current riotous unrest is this: The people in the streets—protesting, looting, gawking, whatevering—are operating in a media-drenched environment. That is, they are in the news, they are making news, and, as “newsmakers,” we know exactly who they are.
Knowing their identity: That’s the key to settling up accounts. Maybe not right away, but eventually.
Yes, the hundreds of thousands, even millions, of people in the streets are becoming media figures of a kind. Together, they are famous, or notorious, and yet individually, they are known to us. That is, the computer cloud sees all, and knows all. The cloud can identify each individual involved—including all the criminals and their criminal acts. So the challenge is to access that cloud, on behalf of law and order.
Yet for the times being, this craziness is just instant fodder for social media. Here, for example, is a tweet video of woke hipsters saluting protesters—and getting their windows smashed with rocks. Is this news? Sure it is. For one thing, it reminds us that naive wokesters don’t understand whom they are dealing with when they cheer on thugs, and yet the video is news, as well, of a crime that was just committed.
Or how ’bout this: looters using a fork-lift to smash their way into a Best Buy. Is that news? In a micro-sense, you bet it is: It’s certainly news that Best Buy can use, and every other property owner for defense. Or this: spray-painting rioters in Boston defacing the “Glory” monument to black soldiers in the U.S. Civil War. That’s news that the current thuggery is the opposite of legitimate civil rights activism.
Indeed, crimes are being committed that are ridiculous, and, at the same time, savage, such as this video of a looter being looted. Or this crazy naked man, attacking and being attacked.
Yet the newest news also includes plenty of viciousness and tragedy, including violent assaults on persons, and even murders. And it’s typically the case that the first report comes from someone’s mobile phone—quite possibly, from the phone of one of the perpetrators.
In fact, each perp—as well as each person—is leaving not only a data trail, but also a metadata trail, concerning their geographic location, plus whatever other data might be being recorded by an app on their mobile.
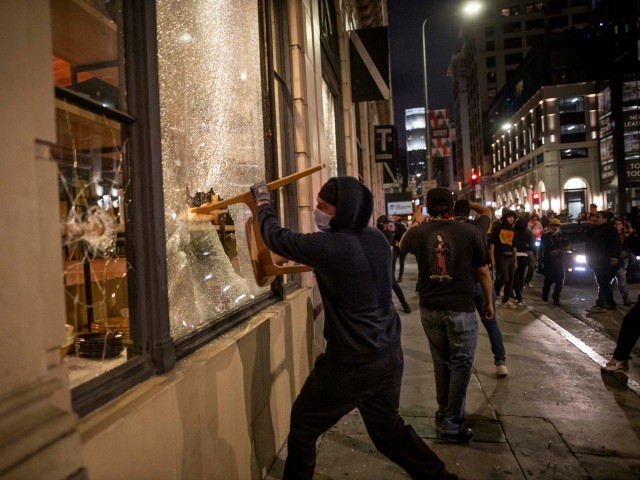
A protester breaks a window with a chair during a protest in downtown Los Angeles, Friday, May 29, 2020. (AP Photo/Christian Monterrosa)
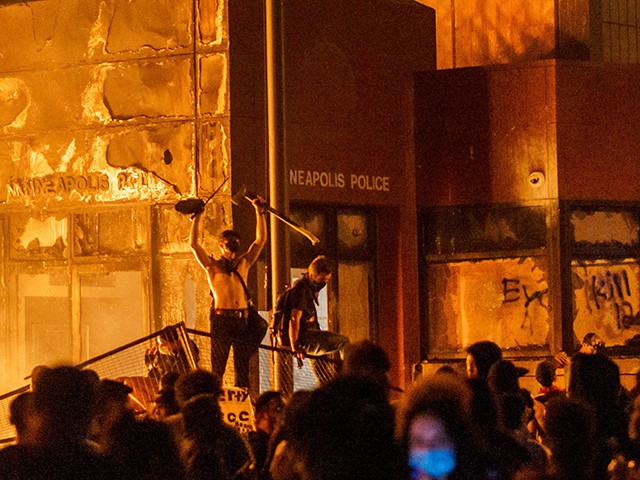
Flames from a nearby fire illuminate protesters standing on a barricade in front of the Third Police Precinct on May 28, 2020, in Minneapolis, Minnesota, during a protest over the death of George Floyd. The precinct, which police had abandoned, burned after a group of protesters pushed through barriers around the building, breaking windows and chanting slogans. A much larger crowd demonstrated as the building went up in flames. (KEREM YUCEL/AFP via Getty Images)

Protesters capture suspect destroying sidewalk in a video posted online amid protests in D.C. on May 31, 2020. Later in the clip, the suspect is handed over to police. (s_Allahverdi/Twitter, screenshot)
The density of this digital mesh is, in fact, astonishing. In America today, some 300 million mobile phones are in use, and of these, more than 275 million are smart phones—and an iPhone produces vastly more data than an antique Motorola.
We can further add that virtually every young person—the demographic most likely to be out on the streets—has a mobile phone; according to a 2018 report from the Pew Center, 99 percent of Americans between the ages of 18 and 49 have mobile phones, and of these, 19 in 20 have smart phones.
Each of these devices produces a daily torrent of data, measured in megabytes or even gigabytes, beaming first to cell phone towers (there were 307,000 such towers in the U.S. in 2016), then to switching centers and servers, and then to other devices.
Of course, there’s a permanent record of all this data. That’s the whole point of the economics that undergird digital technology: The value to a wireless company, such as, say, Verizon, isn’t just the fees paid for the monthly data plan; it’s also the value of the data as it’s sold or rented to marketers and other researchers. Thus every byte ends up being algorithm-ed by a googol of data-crunchers and advertisers.
In addition, every app on a phone builds a file on its user. It’s all perfectly legal—unless, of course, someone is stealthily breaking the terms of those End Use License Agreements, the document that nobody reads before clicking “agree,” and that nobody would understand if they did read it.
Also, let’s not forget our data-hungry government: Even before the 2013 revelations of former National Security Agency contractor Edward Snowden—the nogoodnik who leaked everything he could before defecting to Russia, where he lives as a fugitive to this day—we all sort of knew that the NSA was monitoring our communications.
So now, if we step back to gain perspective about these billion haystacks of data, we can see: It’s easy for a computer to thresh out the needles in each of those haystacks. After all, that’s what artificial intelligence (AI) is all about—finding the needles in each haystack.
Today, corporate America looks for needles of marketing opportunities, and the federal government looks for needles of foreign terrorists and other kinds of criminals. And now, since we have so many more criminals in the wake of the rioting, there are even more needles to seek, and to find.
Thus, in reaction to all this street violence, an easy solution presents itself: Let’s identify all the needles that have been out in the streets, committing crimes. After all, they aren’t even hiding in haystacks; they’re all out in the open—except, of course, when they’re inside looting stores. And when they emerge from their plundering, when they’re burdened with loot, they’re even easier to identify.
In other words, all the needles of crime are right there in front of us. Thus we have the setup for a giant Digital Dragnet—an infinitely bigger dragnet for crooks, in fact, than the classic TV show ever imagined. Let’s use big data to identify each and every protester, and then, operating within that data set, let’s figure out who’s a criminal.
Fortunately, criminals tend to be not very smart. And so they haven’t thought about the fact that they are carrying, on their person, the cellular tool for their detection. Indeed, some of them are so happy in what they are doing—criminals tend to have short time-horizons, as well as a weak understanding of cause and effect—so that they happily mug for the camera, not thinking about the permanent record being created.
Yet even more sophisticated people—like, say, college students who are vandalizing a downtown for the fun of it—might not have absorbed just what a sophisticated science that mobile phone tracking has become, enabling data miners to find human “ore” with astonishing granularity, mapping human movements down to the individual level. That’s why, for example, Apple’s Find My iPhone works so well.

People are seen looting the Apple store at the Grove shopping center in the Fairfax District of Los Angeles on May 30, 2020. (VALERIE MACON/AFP via Getty Images)
In fact, these phone-tracking devices work even when the phone is turned off. And that’s why Apple also knows the location of each one of its looted phones; so now, after they have been “liberated”—that is, heisted from an Apple store—the new proud “liberator” turns it on and sees a message that reads, “This device has been disabled and is being tracked. Local authorities will be alerted.”
For the moment, of course, Apple is striking the pose of a woke company, and so any notion of working with law enforcement is not currently a part of its PR vocabulary.
Yet still, corporate wokeness never seems to get in the way of the corporate bottom line. So yes, Apple believes that Black Lives Matter, but it also believes that iPhones Matter—and it wants them back, or, failing that, wants to make sure that anybody who wants a working iPhone will have to actually pay for it.
Deepening the Dragnet
So we can see, cell phone data is robust. And it’s about to get a lot more robust. We might recall, after all, that up until a few days ago, authorities were intensely interested in knowing people’s precise whereabouts, so as to test them for Covid-19. Indeed, the recent CARES legislation—the $2 trillion package of relief signed into law by President Trump in March—included $500 million for the Centers for Disease Control to develop a new “surveillance and data collection system.”
Now we can realize that there’s another virus—namely, wanton criminality—that we need also need to track. So yes, indeed, let’s track the dangers to our society; we might well discover the violence is the worse virus.
We might also note that mobile phone data is not the only kind of data that we possess; we also have security cameras. In 2019, the Project on Government Oversight of government estimated that 30 million security cameras were in use; each is capturing footage 24/7.
Moreover, security cameras have now been joined by home-security video products, such as Amazon Ring, which, nationwide, is integrated in with more than 1,000 police departments. As was noted here at Breitbart News, Amazon is, in fact, in the process of turning its home-security system into a kind of show—a reality show of whatever happens outside one’s front door, which can, all too often, be a violent reality show.
In addition, according to the Federal Aviation Administration, there are more than 1.5 million drones registered with authorities—and who knows how many more drones are in existence. So we can see: lots of video, and other data, from all those unmanned aerial vehicles.
So how many helicopters, and other aircraft, do authorities have? Numbers from back in 2007 suggest that more than 200 police departments across the U.S. have aviation units, operating more than 900 aircraft—almost all of these helicopters. Helicopters are great for surveillance.
And so what to do with this surveillance capacity? We can also note that facial recognition is one of the hottest fields in tech right now. A good AI program can scan a crowd and identify each person. In fact, a really good AI program can identify even those wearing masks—just from their eyes and cheekbones. And there’s also gait recognition; that is, AI can ID someone by the way he or she walks; no mask can hide that.
Cracking Cases
As we have seen, all this data is sitting there, waiting to be used. At the moment, it’s in many different corporate and government silos, and plenty of laws and taboos prevent it from being aggregated into one holistic, and actionable, database. (This was the problem we faced prior to 9/11, when the CIA and FBI were prevented from sharing information about terrorists; necessarily, the law was soon thereafter changed.)
Yes, the data are still all there, waiting for us. So now what’s needed is the political will to put law enforcement to the task of tracking domestic marauders; a few legal changes, and a few hundred subpoenas, would get the job done. To be sure, it’s far from obvious that the political will exists do any of this data-consolidating, and thus case-closing; the Democrats, many of them deeply invested in riot ideology, will oppose it, and so will many libertarians. If the opposition succeeds, then good times for thugs.
Still, in the meantime, good police work is weaving the available data threads into a knowledge-tapestry of criminality. For instance, on May 31, New York City’s deputy police commissioner for counter-terrorism, John Miller, outlined his analysis of the violence:
Before the protests began organizers of certain anarchist groups set out to raise bail money and people who would be responsible to be raising bail money, they set out to recruit medics and medical teams with gear to deploy in anticipation of violent interactions with police.
In other words, this was, in no small part, a conspiracy. Which explains why, for instance, stacks of bricks for protesters to throw through windows—or at cops’ heads—were placed all around New York City. Heck, stacks of projectiles were even placed in Kansas City, Missouri. (Did we mention that satellite surveillance, too, could play a role in tracking such obvious major movements?) On June 6, Antifa observer Andy Ngo tweeted that two men driving a car with Ohio license plates were arrested in New York City; the vehicle was full of weapons, burner phones, gas masks, everything a terrorist might want.
Two men in a car w/Ohio plates were arrested at the NYC riot. They were found with a cache of weapons & items in their car like knives, a machete, gasoline, radios, burner phones, bricks, gas masks & more. Their names have not been released yet. #antifa https://t.co/7HOoUNSn5f pic.twitter.com/by639zlZwx
— Andy Ngô (@MrAndyNgo) June 6, 2020
As an aside, some might ask: While the NYPD was doing all this good work, where was the FBI? Oh yes, we remember: Much of the FBI’s Deep Statist leadership was too busy trying to frame Michael Flynn. Maybe the FBI should try a little harder to unravel conspiracies, not create its own.
Belatedly, we’re starting to realize how deeply the terrorist network has penetrated our society. We know, now, that they’ve been using Twitter as a tool, and Reddit, too, among many familiar apps and media. They have their own network of partially George Soros-funded lawyers. And yes, there was the curious case of the molotov-cocktail woman in New York City whose $250,000 bail was guaranteed by a lawyer who had previously worked in the federal government, handling highly classified documents, for Barack Obama. Perhaps a thread or two hereto unravel. And speaking of Soros, on June 4, James O’Keefe of Project Veritas revealed undercover video of a vicious Antifa group in Portland, Oregon, which seems to have many connections to Sweden, as well as to, yes, that same Hungarian-born billionaire.
BREAKING: @Project_Veritas INFILTRATED ANTIFA
“Practice things like an eye gouge. It takes very little pressure to injure someone’s eyes.”
“It’s not boxing, it’s not kickboxing, it’s like destroying your enemy.” #EXPOSEANTIFApic.twitter.com/tbLeuXucHx
— James O’Keefe (@JamesOKeefeIII) June 4, 2020
So perhaps now is a good time to revisit legislation first proposed last year by Sen. Bill Cassidy of Louisiana, designating Antifa as a terrorist group, thus greatly strengthening law enforcement’s hand; Cassidy was soon joined by Sen. Ted Cruz and other senators. Such legislation, if enacted, would almost certainly guarantee that the president’s recent executive designation of Antifa would survive the inevitable court challenge.
Yet for the moment, the terrorists are more than holding their own—and if the Democrats win this November, they have little to fear, at least in the short run.
However, it’s possible that a tougher regime will come; after all even the Democrats, if they are in charge after November, will have to wise up soon enough, lest the whole country be sacked. And that’s not such a good platform on which to seek reelection. Both parties know that the vast majority of Americans will despise what’s happening—that’s why, for example, by a nearly 2:1 majority, Americans support sending the military into the cities to provide security. In other words, in addition to buying lots of guns, voters will stand ready to endorse law and order—which, these days, inevitably includes tech-detection.
So a strong leader would seek a mandate to change the laws necessary to make it possible to correlate all this data, thereby building a database of every thug and criminal. Then, once we have all this information in hand, we can figure out what to do with it. Should we prosecute all whom we identify? Or merely send most of them all a bill for the damage they have caused?
Surely, a just country that prizes honesty and civic responsibility would declare, first, that those who have committed felonies shouldn’t be allowed to vote, and second, that those who owe lots of money should have that debt weighed against future benefits, starting with student financial aid, and including the future garnishing of wages and dividends.
So we can see: The Digital Dragnet could not only punish the heinously guilty, it could also pay for itself with money seized from fun-loving Antifa youths—or from their parents, or from their trust funds.
via Breitbart News
Enjoy this article? Read the full version at the authors website: https://www.breitbart.com
